- Mifare Classic Offline Cracker Box
- Mifare Classic Offline Cracker Barrel
- Mifare Classic Offline Cracker Recipe
MIFARE Classic offline cracker: mfoc-0.10.7: mfterm: Terminal for working with Mifare Classic 1-4k Tags: todo: rfdump: tool to decode RFID tag data: todo. MfocGUIv29 Mifare Offline Cracker GUI + OV Data Interpreter. MFOC is an open source implementation of 'offline nested' attack by Nethemba. This program allow to recover authentication keys from MIFARE Classic card. Please note MFOC is able to recover keys from target only if it have a known key: default one (hardcoded in MFOC) or custom one (user provided using command line).
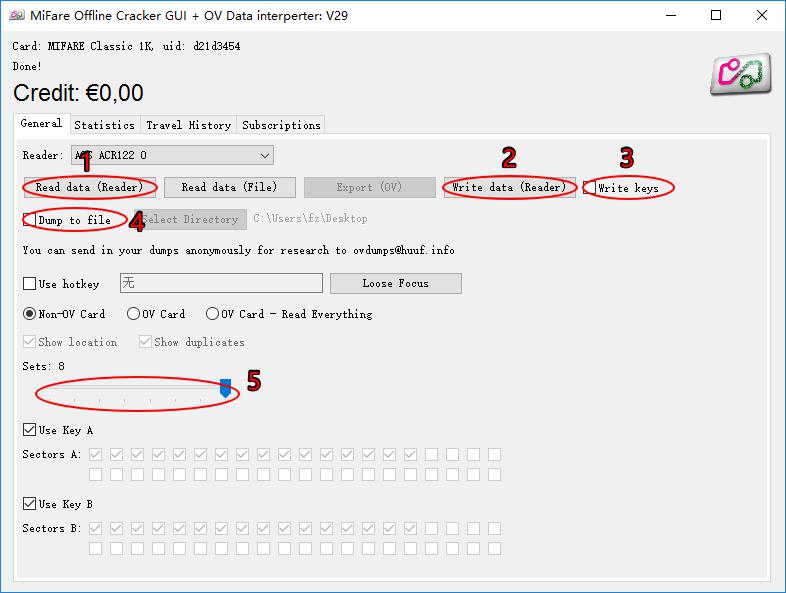
Feb 01, 2019 MFOC – MiFare classic Offline Cracker. The easiest and most basic tool to use against MIFARE tags, is MFOC. It tries different keys against a MIFARE tags. Once MFOC finds a correct key the tool can “guess” the other keys and dump the memory of the tag. (Figure 2.2) MFOC attack – Figure 2.2. Here is a basically memory layout of a Mifare Classic tag: taken from the Mifare Datasheet, link see below More about Mifare in general can be found on. There is no need to hard wire when installing this proximity lockset and this unit features the latest in Mifare technology to provide a networked electronic locking solution with an extensive.
Mifare Classic Offline Cracker Box

Mifare Classic Offline Cracker Barrel
Nethemba public security research projects (2007-2015)
Mifare Classic Offline Cracker Recipe
Since 2007 when Nethemba was started, we have begun to focus on public research projects. One of the reasons was that we were aware of a lack of security in technologies most people use daily, the second one, was a need of being different compared to our IT security competition, especially in Czech and Slovak republic. During the period 2007-2015, we published many security-related articles, blogs, and papers. We would like to discuss the most important ones with the considerable impact.