- John The Ripper 0 Password Hashes 1 Left Hand Piano
- John The Ripper 0 Password Hashes 1 Left Hand Thread
- John The Ripper 0 Password Hashes 1 Left Hand
- John The Ripper 0 Password Hashes 1 Left Hand Bolt
Want to get started with password cracking and not sure where to begin? In this post we’ll explore how to get started with it.
Most systems don’t store passwords on them. Instead they store hashes of passwords and when authentication takes place, the password is hashes and if the hashes match authentication is successful. Different systems store password hashes in different ways depending on the encryption used.
Password hash cracking usually consists of taking a wordlist, hashing each word and comparing it against the hash you’re trying to crack. This is a variation of a dictionary attack because wordlists often are composed of not just dictionary words but also passwords from public password dumps. This type of cracking becomes difficult when hashes are salted).
A previous session can be retrieve thanks to john.rec file. To restore a session, issue: $./john -restore Retrieve cracked passwords. To retrieve cracked passwords (in this example, no password has been cracked, session has been aborted): $./john -show /etc/shadow 0 password hashes cracked, 2 left. This module uses John the Ripper to identify weak passwords that have been acquired as hashed files (loot) or raw LANMAN/NTLM hashes (hashdump). The goal of this module is to find trivial passwords in a short amount of time. To crack complex passwords or use large wordlists, John the Ripper should be used outside of Metasploit. This initial version just handles LM/NTLM credentials from. Nov 10, 2015 Cracking password using John the Ripper. In Linux, password hash is stored in /etc/shadow file. For the sake of this exercise, I will create a new user names john and assign a simple password ‘password’ to him. I will also add john to sudo group, assign /bin/bash as his shell. $ john-the-ripper.zip2john SantaGramv4.2.zip zip2.hash ver 2.0 efh 5455 efh 7875 SantaGramv4.2.zip-SantaGram4.2.apk PKZIP Encr: 2b chk, TSchk, cmplen=1962826, decmplen=2257390, crc=EDE16A54 $ john-the-ripper zip2.hash Using default input encoding: UTF-8 Loaded 1 password hash (PKZIP 32/64) Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status 0g 0:00. Option) might be already cracked by previous invocations of John. (The message printed in that case has been changed to 'No password hashes left to crack (see FAQ)' starting with version 1.7.7.) To display cracked passwords, use 'john -show' on your password hash file(s). To force John to crack those same hashes again, remove the john.pot file.
The tool we are going to use to do our password hashing in this post is called John the Ripper. John is a great tool because it’s free, fast, and can do both wordlist style attacks and brute force attacks. A brute force attack is where the program will cycle through every possible character combination until it has found a match.
Setup
To get setup we’ll need some password hashes and John the Ripper.
Sample Password Hashes
A group called KoreLogic used to hold DEFCON competitions to see how well people could crack password hashes. Their contest files are still posted on their site and it offers a great sample set of hashes to begin with.
Download the password hash file bundle from the KoreLogic 2012 DEFCON challenge.Or use this mirror.
Extract the file using this linux command:
This expands into 19 different hashdumps including des, md5, and ntlm type encryption. Each of the 19 files contains thousands of password hashes. This should be a great data set to test our cracking capabilities on.
John the Ripper
Next we’ll need the cracking tool itself. If you’re using Kali Linux, this tool is already installed. Download John the Ripper here. In my case I’m going to download the free version John the Ripper 1.8.0 (sources, tar.gz, 5.2 MB).
Once downloaded, extract it with the following linux command:
Then follow the instructions in docs/INSTALL to complete the install.
Getting a Wordlist
We’ll need a good wordlist to go through to see if any passwords in it, match our hashes.
- A basic word list containing 3,559 words can be found bundled in the John the Ripper tarball in the run dir. This is a list of the most common passwords seen in public hash dumps.
- If using Kali linux, a good size wordfile is located at
/usr/share/wordlists/rockyou.txt.gz. Unzip it withgunzipand you’ve got a good wordfile to workwith. - A large word list containing 1,493,677,782 words can be found at crackstation.
The size word list you need depends on your needs. If you have a large hashdump, chances are even cracking 5% of the hashes will result in a victory, which may get you admin access. But if you have a only one password hash, you’ll need 100% success rate and probably need a bigger wordlist.

Basic John Usage
Use John to begin the cracking with this command:
This simple command does the following:
- Detected there are 10,297 password hashes in the file and their salts.
- Auto detected the passwords were DES encrypted
- Will first attempt single crack mode
- Will then attempt to use the built in wordlist (most common passwords) to crack passwords
- Will then go into incremental mode
Checking Status
While John the Ripper is running, press any key (like enter) to see a status output. Or to check from another terminal you can run john --status. The output looks like this:
Here is what each section means:
- Type of encryption it is trying to crack with
- Number of successful password guesses
- Time elapsed since started
- Percent completed for that pass
- Current pass / number of passes total
- g/s = successful guesses per second
- p/s = passwords tested per second
- c/s = crypts (password hashes) computed per second
- C/s = crypts tested per second (in versions below 1.8.0 this was “c/s”)
- The current word it’s trying.
Passes/Modes
John has three modes to attempt to crack hashes. If you do not indicate the mode, all 3 will be used and you will see x/3 in your status output indicating which mode it’s on.
See http://www.openwall.com/john/doc/MODES.shtml for detailed description of each mode.
John The Ripper 0 Password Hashes 1 Left Hand Piano
(1) Single Crack
This mode attempts to mangle the username and try it as the password. Example: if the username was “jackson” it would try the following passwords:
jackson
JACKSON
jackson1
j-ackson
Jackson=
jacks0n
It tries hundreds of variations of the username. It tries this password on all hashes in your file so the more usernames you give it, the greater chance of it finding something in the single crack mode.
This is a great mode to start with because it’s the fastest and sometimes works wonderfully.
John The Ripper 0 Password Hashes 1 Left Hand Thread
To just use this mode do the following:
(2) Wordlist Mode
In this mode, John is using a wordlist to hash each word and compare the hash with the password hash. If you do not indicate a wordlist, John will use the one it comes bundled with which has about 3,500 words which are the most common passwords seen in password dumps.
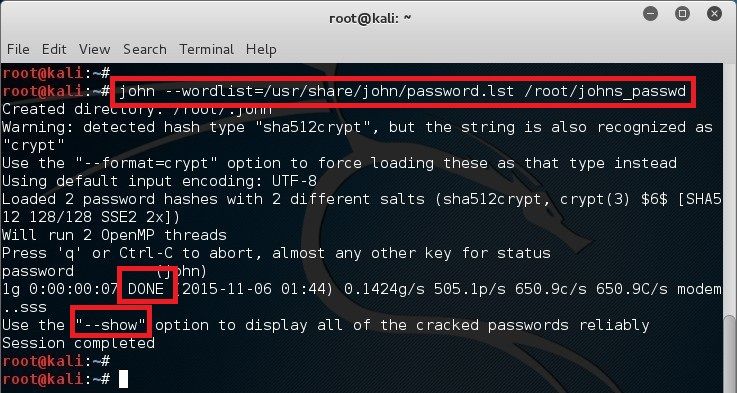
To use try just the wordlist mode do the following:
(3) Incremental
Attempts a brute force style attack, trying every combination of characters possible. This type of attempt will never complete because it will just keep trying higher and higher password lengths.
To try just the incremental mode, do this command:

Word mangling rules
John The Ripper 0 Password Hashes 1 Left Hand
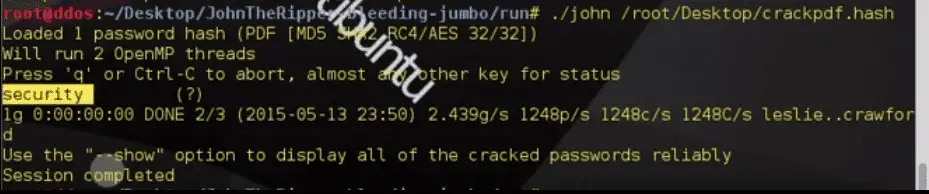
John has the ability to take a wordlist and mangle the words in it to try variations of that word. It will add numbers to the end of the word and try replacing letters with numbers and adding other random symbols. So if the word list contains the word jackson, with rules turned on it would try each of these plus hundreds more.
jackson
JACKSON
jackson1
j-ackson
Jackson=
jacks0n
By simply enabling --rules when invoking John, the mangling rules applied are usually decent. However, you can modify the config file to alter the way the mangling is done. Read here for further information on how to do that:
Additionally you can see what others have used for rules like KoreLogic:
Final Example
To use a larger word list, with DES encryption only, and rule mangling turned on, use the following:
The best way to get John to run in the background is using the standard linux screen command.