John the Ripper is part of Owl, Debian GNU/Linux, Fedora Linux, Gentoo Linux, Mandriva Linux, SUSE Linux, and a number of other Linux distributions. It is in the ports/packages collections of FreeBSD, NetBSD, and OpenBSD. John the Ripper is a registered project with Open Hub and it is listed at SecTools. John the Ripper’s primary modes to crack passwords are single crack mode, wordlist mode, and incremental. The single crack mode is the fastest and best mode if you have a full password file to crack. Wordlist mode compares the hash to a known list of potential password matches. Incremental mode is the most powerful and possibly won’t complete. Gimp 2.8 22 X8664 Dmg Make Bootable 10.6 Disc From Dmg File Mechanism That Repairs Uv Dmg Can I Delete Javaforosx.dmg On My Mac Dmg Innovation Days New Hampshire Dmg File Extractor For Windows 8 Does A Gameboy Pocket Fit Into A Regualar Gameboy Dmg-01 John The Ripper Oxs Dmg Roll20 Higher Level Cast Dmg.
|
John the Ripper password cracker.
John the Ripper is a fast password cracker, currently available formany flavors of Unix, macOS, Windows, DOS, BeOS, and OpenVMS (the latterrequires a contributed patch). Its primary purpose is to detect weakUnix passwords. Besides several crypt(3) password hash types mostcommonly found on various Unix flavors, supported out of the box areKerberos/AFS and Windows LM hashes, as well as DES-based tripcodes, plushundreds of additional hashes and ciphers in '-jumbo' versions.
John The Ripper Download
How to install.
See INSTALL for information on installing John on your system.
How to use.
To run John, you need to supply it with some password files andoptionally specify a cracking mode, like this, using the default orderof modes and assuming that 'passwd' is a copy of your password file:
or, to restrict it to the wordlist mode only, but permitting the useof word mangling rules:
Cracked passwords will be printed to the terminal and saved in thefile called $JOHN/john.pot (in the documentation and in theconfiguration file for John, '$JOHN' refers to John's 'homedirectory'; which directory it really is depends on how you installedJohn). The $JOHN/john.pot file is also used to not load passwordhashes that you already cracked when you run John the next time.
To retrieve the cracked passwords, run:
While cracking, you can press any key for status, or 'q' or Ctrl-C toabort the session saving its state to a file ($JOHN/john.rec bydefault). If you press Ctrl-C for a second time before John had achance to complete handling of your first Ctrl-C, John will abortimmediately without saving. By default, the state is also saved every10 minutes to permit for recovery in case of a crash.
To continue an interrupted session, run:
These are just the most essential things you can do with John. Fora complete list of command line options and for more complicated usageexamples you should refer to OPTIONS and EXAMPLES, respectively.
Please note that 'binary' (pre-compiled) distributions of John mayinclude alternate executables instead of just 'john'. You may need tochoose the executable that fits your system best, e.g. 'john-omp' totake advantage of multiple CPUs and/or CPU cores.
Features.
John the Ripper is designed to be both feature-rich and fast. Itcombines several cracking modes in one program and is fullyconfigurable for your particular needs (you can even define a customcracking mode using the built-in compiler supporting a subset of C).Also, John is available for several different platforms which enablesyou to use the same cracker everywhere (you can even continue acracking session which you started on another platform).
Out of the box, John supports (and autodetects) the following Unixcrypt(3) hash types: traditional DES-based, 'bigcrypt', BSDI extendedDES-based, FreeBSD MD5-based (also used on Linux and in Cisco IOS), andOpenBSD Blowfish-based (now also used on some Linux distributions andsupported by recent versions of Solaris). Also supported out of the boxare Kerberos/AFS and Windows LM (DES-based) hashes, as well as DES-basedtripcodes.
When running on Linux distributions with glibc 2.7+, John 1.7.6+additionally supports (and autodetects) SHA-crypt hashes (which areactually used by recent versions of Fedora and Ubuntu), with optionalOpenMP parallelization (requires GCC 4.2+, needs to be explicitlyenabled at compile-time by uncommenting the proper OMPFLAGS line nearthe beginning of the Makefile).
Similarly, when running on recent versions of Solaris, John 1.7.6+supports and autodetects SHA-crypt and SunMD5 hashes, also withoptional OpenMP parallelization (requires GCC 4.2+ or recent Sun Studio,needs to be explicitly enabled at compile-time by uncommenting theproper OMPFLAGS line near the beginning of the Makefile and at runtimeby setting the OMP_NUM_THREADS environment variable to the desirednumber of threads).
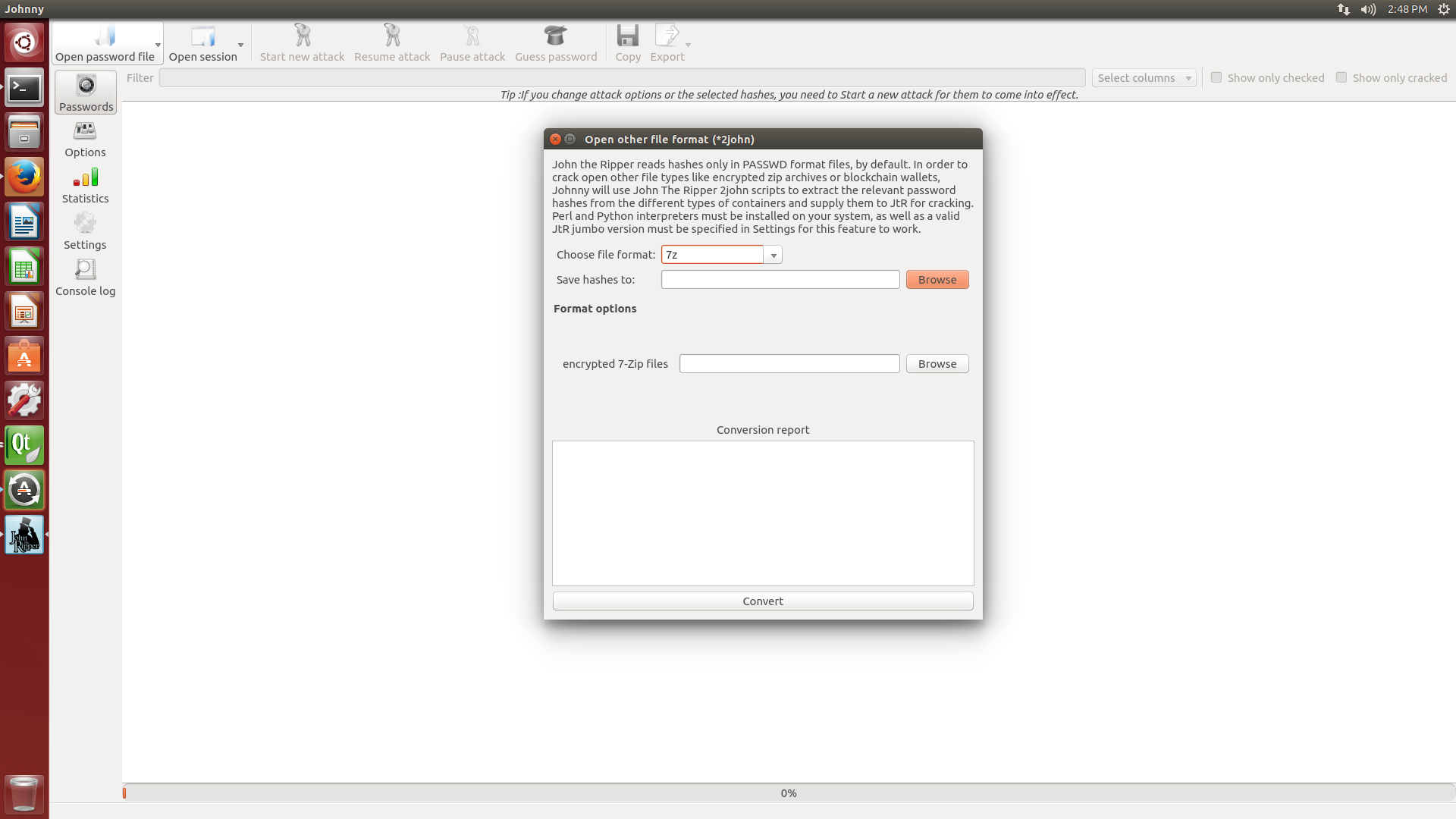
'-jumbo' versions add support for hundreds of additional hash and ciphertypes, including fast built-in implementations of SHA-crypt and SunMD5,Windows NTLM (MD4-based) password hashes, various macOS and Mac OS Xuser password hashes, fast hashes such as raw MD5, SHA-1, SHA-256, andSHA-512 (which many 'web applications' historically misuse forpasswords), various other 'web application' password hashes, various SQLand LDAP server password hashes, and lots of other hash types, as wellas many non-hashes such as SSH private keys, S/Key skeykeys files,Kerberos TGTs, encrypted filesystems such as macOS .dmg files and'sparse bundles', encrypted archives such as ZIP (classic PKZIP andWinZip/AES), RAR, and 7z, encrypted document files such as PDF andMicrosoft Office's - and these are just some examples. To load some ofthese larger files for cracking, a corresponding bundled *2john programshould be used first, and then its output fed into JtR -jumbo.
Documentation.
The rest of documentation is located in separate files, listed here inthe recommended order of reading:
* INSTALL - installation instructions
* OPTIONS - command line options and additional utilities
* MODES - cracking modes: what they are
* CONFIG (*) - how to customize
* RULES (*) - wordlist rules syntax
* EXTERNAL (*) - defining an external mode
* EXAMPLES - usage examples - strongly recommended
* FAQ - guess
* CHANGES (*) - history of changes
* CONTACT (*) - how to contact the author or otherwise obtain support
* CREDITS (*) - credits
* LICENSE - copyrights and licensing terms
* COPYING - GNU GPL version 2, as referenced by LICENSE above
(*) most users can safely skip these.
Happy reading!
$Owl: Owl/packages/john/john/doc/README,v 1.27 2019/04/11 23:52:56 solar Exp $
John the Ripper (JtR) is one of the hacking tools the Varonis IR Team used in the first Live Cyber Attack demo, and one of the most popular password cracking programs out there. In this blog post, we are going to dive into John the Ripper, show you how it works, and explain why it’s important.
Notes about hacking: Hacking is a pursuit of knowledge about systems, design, and humans. In this case, we are talking about software and operating systems.
Get the Free Pen Testing Active Directory Environments EBook
Hacking is not necessarily criminal, although it can be a tool used for bad intentions. We advocate for ethical hacking. Stay in the light side of the Force.
How Does John the Ripper Work?
JtR supports several common encryption technologies out-of-the-box for UNIX and Windows-based systems. (ed. Mac is UNIX based). JtR autodetects the encryption on the hashed data and compares it against a large plain-text file that contains popular passwords, hashing each password, and then stopping it when it finds a match. Simple.
In our amazing Live Cyber Attack demo, the Varonis IR team demonstrates how to steal a hashed password, use JtR to find the true password, and use it to log into an administrative account. That is a very common use case for JtR!
JtR also includes its own wordlists of common passwords for 20+ languages. These wordlists provide JtR with thousands of possible passwords from which it can generate the corresponding hash values to make a high-value guess of the target password. Since most people choose easy-to-remember passwords, JtR is often very effective even with its out-of-the-box wordlists of passwords.
JtR is included in the pentesting versions of Kali Linux.
John The Ripper Github
What is John the Ripper Used for?
JtR is primarily a password cracker used during pentesting exercises that can help IT staff spot weak passwords and poor password policies.
Here is the list of encryption technologies found in JtR:
- UNIX crypt(3)
- Traditional DES-based
- “bigcrypt”
- BSDI extended DES-based
- FreeBSD MD5-based (linux and Cisco IOS)
- OpenBSD Blowfish-based
- Kerberos/AFS
- Windows LM (DES-based)
- DES-based tripcodes
- SHA-crypt hashes (newer versions of Fedora and Ubuntu)
- SHA-crypt and SUNMD5 hashes (Solaris)
That’s the “official” list. JtR is open-source, so if your encryption of choice isn’t on the list do some digging. Someone might have already written an extension for it.
How to Download John the Ripper
JtR is an open-source project, so you can either download and compile the source on your own, download the executable binaries, or find it as part of a penetration testing package.
The official website for John the Ripper is on Openwall. You can grab the source code and binaries there, and you can join the GitHub to contribute to the project.
JtR is available on Kali Linux as part of their password cracking metapackages.
Tutorials for Using John the Ripper
We are going to go over several of the basic commands that you need to know to start using John the Ripper. To get started all you need is a file that contains a hash value to decrypt.
If you ever need to see a list of commands in JtR, run this command:
Cracking Passwords
John the Ripper’s primary modes to crack passwords are single crack mode, wordlist mode, and incremental. The single crack mode is the fastest and best mode if you have a full password file to crack. Wordlist mode compares the hash to a known list of potential password matches. Incremental mode is the most powerful and possibly won’t complete. This is your classic brute force mode that tries every possible character combination until you have a possible result.
The easiest way to try cracking a password is to let JtR go through a series of common cracking modes. This command below tells JtR to try “simple” mode, then the default wordlists containing likely passwords, and then “incremental” mode.
You can also download different wordlists from the Internet, and you can create your own new wordlists for JtR to use with the –wordlist parameter.
If you want to specify a cracking mode use the exact parameter for the mode.
Word Mangling Rules
Mangling is a preprocessor in JtR that optimizes the wordlist to make the cracking process faster. Use the –rules parameter to set the mangling rules.
John The Ripper Dmg Download
Viewing Your Output
When you want to see the list of passwords that you have cracked, use the –show parameter.
If your cracked password list is long, you can filter the list with additional parameters. You can also redirect the output using basic redirection in your shell. For example, if you want to see if you cracked any root users (UID=0) use the –users parameter.
Or if you want to show users from privileged groups use –groups.
Below is the JtR command from our Live Cyber Attack Webinar. In this scenario, our hacker used kerberoast to steal a Kerberos ticket granting ticket(TGT) containing the hash to be cracked, which was saved in a file called ticket.txt. In our case, the wordlist used is the classic rockyou password file from Kali Linux, and the command was set to report progress every 3 seconds.
If you want to see some cool pentesting and defense tactics using Varonis, check out the Live Cyber Attack Webinars! Pick any time that works for you!